This attack is commonly used against remote Linux servers on which SSH service is enabled.
Hydra is a password cracking tool available in Backtrack.
Let the IP address of the server be 192.168.109.134.
So start an nmap scan. For that open terminal and issue the following command:
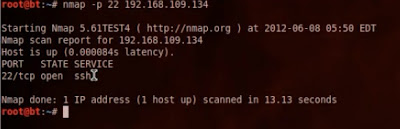
nmap –p 22 192.168.109.134
After the scan is completed, it will show you whether SSH service is enabled at port 22. You can only proceed if the nmap scan shows the result similar to that in the above image.
Now open hydra GUI which is located at BackTrack -> Privilege Escalation -> Password Attacks -> Online Attacks -> hydra-gtk
On the target tab specify the details as follows:
Single Target: 192.168.109.134
Port: 22
Protocol: ssh
Show Attempts: checked
Be Verbose: checked
On the Password tab specify the details as follows:
Username: root //we are assuming that the username is root.
Password List: Select a password list.
On the Tuning tab specify the details as follows:
Number of Tasks: 10
Timeout: 29
Now click on the Start tab and select Start and wait for Hydra to crack the password. The password will be cracked if its there in the password list.
Now after you got the password go to terminal and issue the following command:
ssh 192.168.109.134
root@192.168.109.134’s password:
it will ask for the password give the password and you are in the remote system.
Securing/Protection Against Attack
* Configure SSH in Filtered state.
* Setup a strong password.
* Change the Default Password and User Name.
* Configure the iptables rule to defend against Dictionary attack.
* Make Updates Regularly .
![=-=>>W3LC[]M3<<=-=](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEhKDfXWbxTiIVc3Mpzd5cHDrZosfQsD6U4AO1p-OXMSPw53WXIObbXzVhbwSucaYVwciOWxScMYx7TGvAd5xE9RnH-5Y4m-JMHs7p9K_B3iu7Sju0N8jjbeLkC47MybRRe1R9rA5tl1PFc/s1600/2.jpg)
No comments:
Post a Comment